
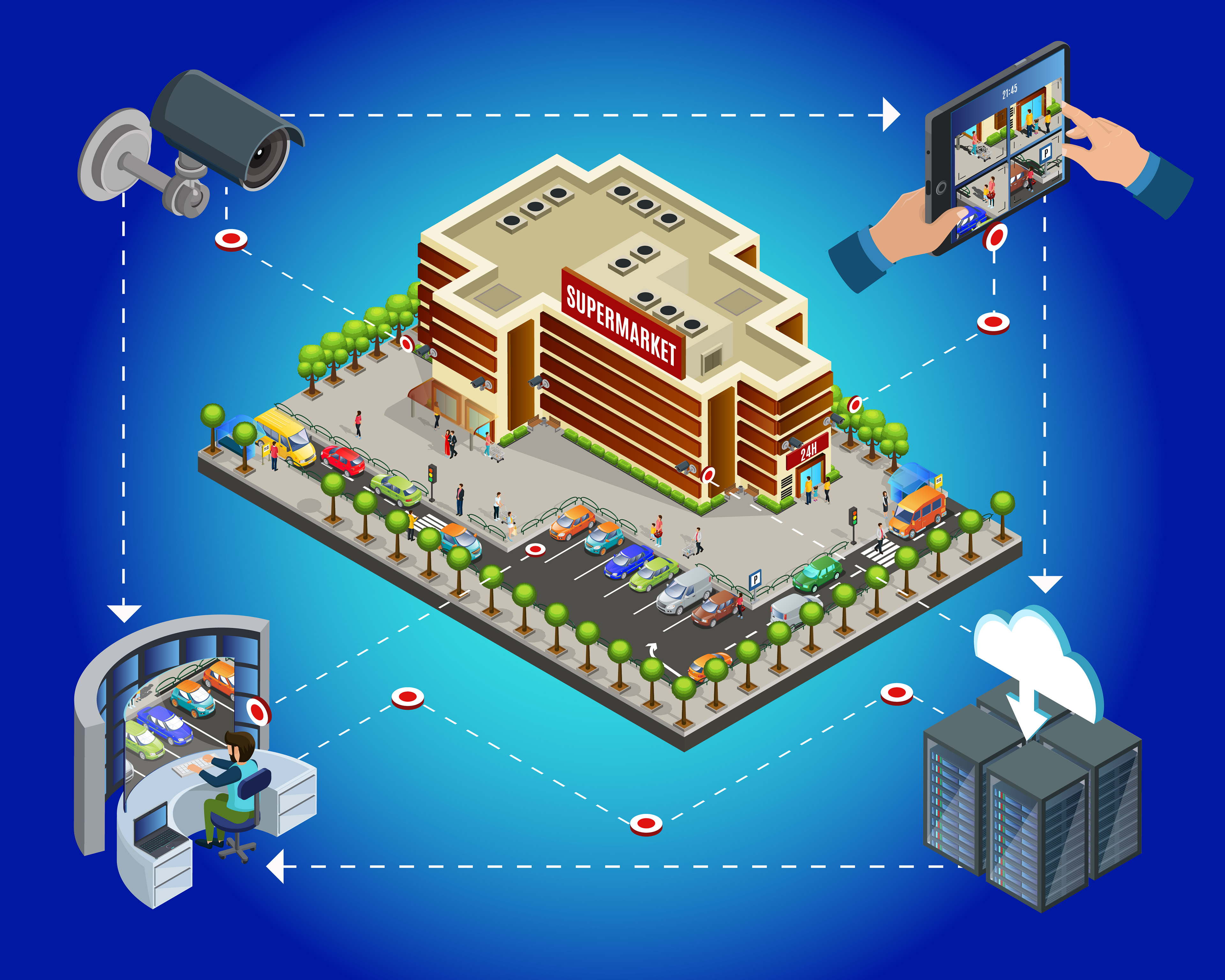
Access control system monitoring involves the continuous oversight and analysis of an access control system's performance and security. This includes real-time monitoring of access logs, system alerts, and security events to detect any anomalies or unauthorized activities. The monitoring process may involve the use of specialized software tools that track user access, authentication attempts, and system events.
Key aspects of access control system monitoring include:
Real-time Alerts: Set up alerts for unusual access patterns, failed authentication attempts, or other security events to enable prompt investigation and response.
User Activity Tracking: Monitoring and recording user activity to ensure compliance with security policies and regulations, and to identify any suspicious behavior.
System Health Monitoring: Regularly check the health and performance of hardware components, such as card readers and controllers, as well as software components, to ensure smooth operation.
Log Analysis: Analyzing access logs and system logs to identify trends, patterns, and potential security threats, such as brute force attacks or insider threats.
Policy Enforcement: ensuring that access control policies are enforced consistently across the system, including user permissions, access levels, and authentication methods.
Security Incident Response: Developing and implementing procedures for responding to security incidents, including containment, investigation, and remediation.
Overall, access control system monitoring is essential for maintaining the security and integrity of the system, as well as for proactively identifying and addressing potential security risks.








