
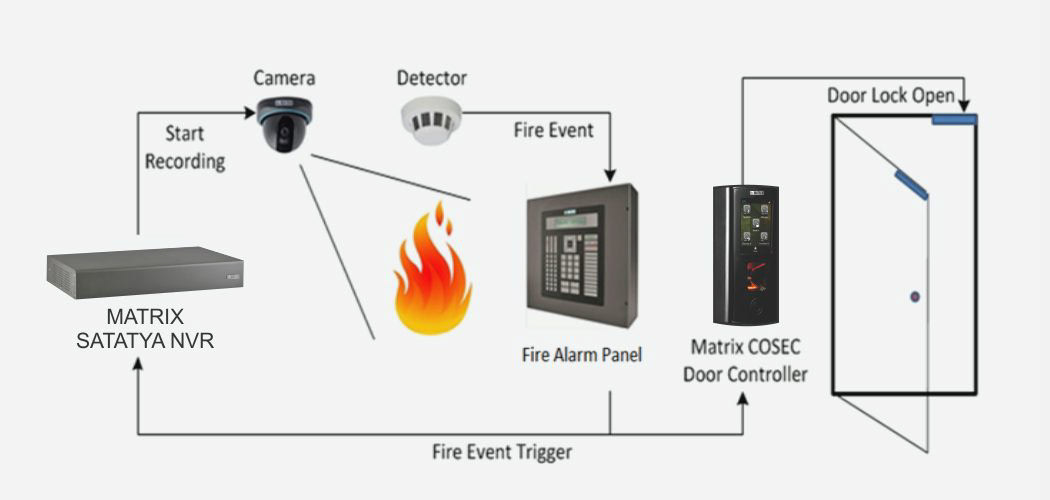
Access control integration with an existing system involves incorporating new access control components or technologies into an already established security infrastructure. This process ensures seamless operation, enhanced functionality, and improved security across the entire system. Here's a brief description of the integration process:
Assessment of Existing System: The integration process begins with a thorough assessment of the current access control system and other related security systems, such as surveillance cameras, alarm systems, and intrusion detection systems. This helps identify any gaps, limitations, or areas for improvement.
Compatibility Check: Technicians evaluate the compatibility of the new access control components or technologies with the existing system. This includes assessing hardware compatibility, software integration capabilities, and communication protocols to ensure smooth integration without disrupting existing operations.
Hardware Integration: If new hardware components, such as card readers, biometric scanners, or control panels, are being added, technicians install and connect these devices to the existing system infrastructure. This may involve wiring, mounting, and configuring hardware to communicate effectively with the rest of the system.
Software Integration: Integration also involves configuring access control software to work seamlessly with the existing software platform or management system. This includes setting up data synchronization, user authentication, access policies, and event logging to ensure consistent operation across all integrated components.
Testing and Validation: Once the integration is complete, technicians conduct rigorous testing to verify the functionality, interoperability, and security of the integrated system. This includes testing access control workflows, data exchange between systems, and responding to security events to ensure proper operation under various scenarios.
Training and Documentation: Training sessions are provided to system administrators, security personnel, and end-users on how to operate and manage the integrated access control system effectively. Documentation, including user manuals, system configurations, and troubleshooting guides, is also provided for reference.
Ongoing Support and Maintenance: After integration, ongoing support and maintenance services are offered to address any issues, perform software updates, and ensure the continued reliability and performance of the integrated access control system. This includes monitoring system health, responding to user inquiries, and conducting periodic system audits.
Overall, access control integration with an existing system aims to leverage existing investments, enhance security capabilities, and provide a cohesive and comprehensive security solution tailored to the specific needs of the organization.








